Table of Contents
Great systems are not just built. They are monitored.
MetricFire is a managed observability platform that helps teams monitor production systems with clean dashboards and actionable alerts. Delivering signal, not noise. Without the operational burden of self-hosting.
Introduction
The past decade has seen a drastic growth in the adoption of public cloud. One of the primary reasons for this is its cheaper infrastructure and ease of scale. With such rapid adoption of public cloud, the need for infrastructure automation also arises.
This is because teams want to quickly provision infrastructure and automate tasks that previously took weeks in the case of traditional data centers, down to minutes in the public cloud. In order to perform these tasks, we need cutting-edge cloud automation tools and cloud integration that not only help with this but are also easy to use and learn.
With so much automation across the board, and such complex architecture hosting your business’ critical applications, it is immensely important that you have correct infrastructure monitoring in place. Your monitoring stack should be able to provide you with an in-depth view of your application and infrastructure’s performance.
This way, you can make the right business decisions and tap into your infrastructure’s potential. MetricFire can help you ensure that these metrics are monitored properly and allow you complete insight into your application’s performance.
MetricFire specializes in monitoring systems and you can use your product with minimal configuration to gain in-depth insight into your environments.
If you would like to learn more about how MetricFire can help monitor your environments, please book a demo with us, or sign up for the free trial today.
Today we will learn about the seven best cloud automation tools and factors to consider when choosing one of them.
Key Takeaways
- Infrastructure automation tools enable quick provisioning and automation of tasks that used to take weeks in traditional data centers but can now be done in minutes in the public cloud.
- Correct infrastructure monitoring is crucial in complex cloud architectures to gain insights into application and infrastructure performance.
- The article discusses seven top cloud automation tools, including Ansible, Chef, Puppet, SaltStack, Terraform, AWS CloudFormation, and Kubernetes.
- Organizations should select the appropriate cloud automation tool based on their specific needs and requirements.
- Proper cloud automation and monitoring tools are essential for organizations to meet SLAs and ensure operational efficiency.
Best Cloud Infrastructure Automation Tools
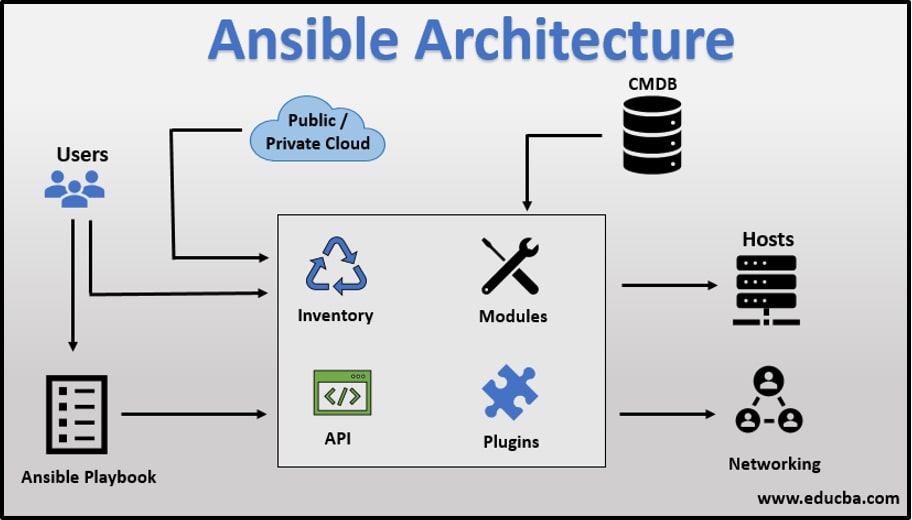
Ansible
You can use Ansible to automate three types of tasks:
- Provisioning: Set up the various servers you need in your infrastructure.
- Configuration management: Change the configuration of an application, OS, or device; start and stop services; install or update applications; implement a security policy; or perform a wide variety of other configuration tasks.
- Application deployment: Make DevOps easier by automating the deployment of internally developed applications to your production systems.
Ansible can automate IT environments whether they are hosted on traditional bare metal servers, virtualization platforms, or in the cloud. It can also automate the configuration of a wide range of systems and devices such as databases, storage devices, networks, firewalls, and many others.
The best part is that you don’t even need to know the commands used to accomplish a particular task. You just need to specify what state you want the system to be in and Ansible will take care of it. For example, to ensure that your web servers are running the latest version of Apache, you could use a playbook similar to the following and Ansible would handle the details.
---
- hosts: webservers
vars:
http_port: 80
max_clients: 200
remote_user: root
tasks:
- name: ensure apache is at the latest version
yum: name=httpd state=latest
- name: write the apache config file
template: src=/srv/httpd.j2 dest=/etc/httpd.conf
notify:
- restart apache
- name: ensure apache is running (and enable it at boot)
service: name=httpd state=started enabled=yes
handlers:
- name: restart apache
service: name=httpd state=restarted
The line in the above playbook that actually installs or updates Apache is “yum: name=httpd state=latest”. You just specify the name of the software package (httpd) and the desired state (latest) and Ansible does the rest. The other tasks in the playbook update the Apache config file, restart Apache, and enable Apache to run at boot time.
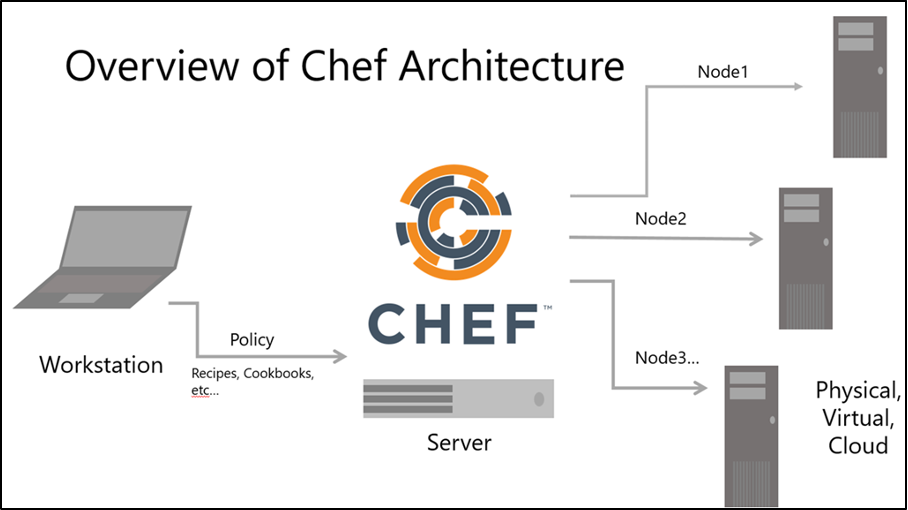
Chef
Chef is one of the oldest and best-known infrastructure automation tools out there. It scales easily and can be used to manage 5 servers or 5,000. It facilitates continuous delivery and configuration management. By converting infrastructure to code, Chef enables IT professionals and cloud engineers to automate the building, deployment, and management of infrastructure.
Key Features:
- Automation of tasks by employing reusable definitions
- You can use the predefined resources as building blocks or define your own
- Test code on a local workstation or isolated environment before deploying into production
- Automated testing for security and compliance
- Dashboards for infrastructure management, auditing, and troubleshooting
Puppet
Puppet, available in both open-source and commercial versions, has its own language, the eponymous Puppet. As with other DevOps programs, Puppet automates changes, eliminating manual script-driven changes. However, Puppet is not simply another shell language, such as Windows PowerShell or Unix and Linux's Bash shells.
Nor is Puppet a pure programming language, such as PHP. Instead, Puppet uses a declarative, model-based approach to IT automation. This enables Puppet to define infrastructure as code and enforce system configuration with programs.
In Puppet, the configuration management tool syntax is decoupled from the underlying operating systems and applications' syntax. This enables you to define high-level concepts such as user, application, and service. Puppet then translates these higher-level concepts into the operating system and software setup instructions.
Puppet models everything as data: the node's current state, the desired end state, and the actions needed to move from one to the other. Each Puppet-managed server instance receives a catalog of resources and relationships, compares it with the desired system state, and makes changes as needed to bring the system into compliance with the ideal state.
You use these programs to manage all of the software, services, and configuration on given systems, with the end goal of building complete system configurations in code. This is considered quite challenging.
MetricFire specializes in monitoring systems and you can use your product with minimal configuration to gain in-depth insight into your environments.
If you would like to learn more about how MetricFire can help monitor your environments, please book a demo with us, or sign up for the free trial today.
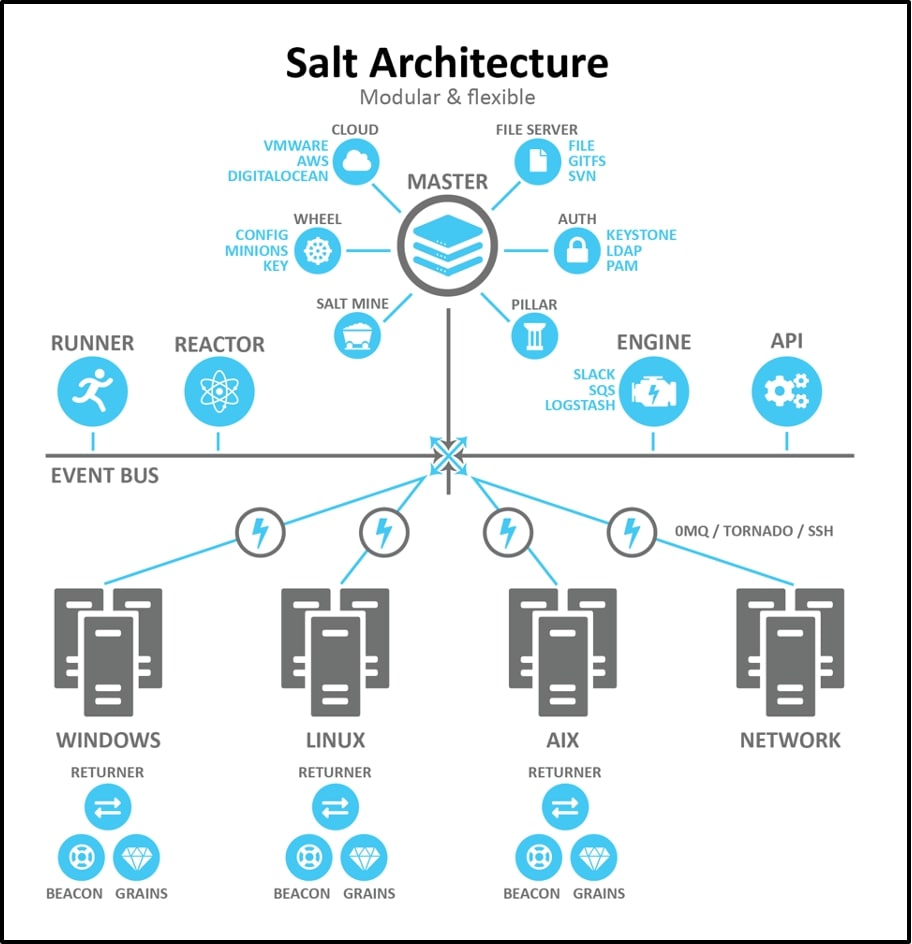
SaltStack
SaltStack is an established name in infrastructure automation. It approaches IT management by creating software that is easy to use, fast, and scalable. SaltStack provides a dynamic communication bus for orchestration, configuration management, and remote execution.
Since it was launched in 2011, SaltStack has been one of the most active and fastest-growing infrastructure automation projects in the world.
Key Features:
- Multi-cloud orchestration
- Instant audit of security policies
- Continuous code integration and deployment
- Data filtering and event aggregation ensure efficient data management
- Can run agentless or with a resilient agent
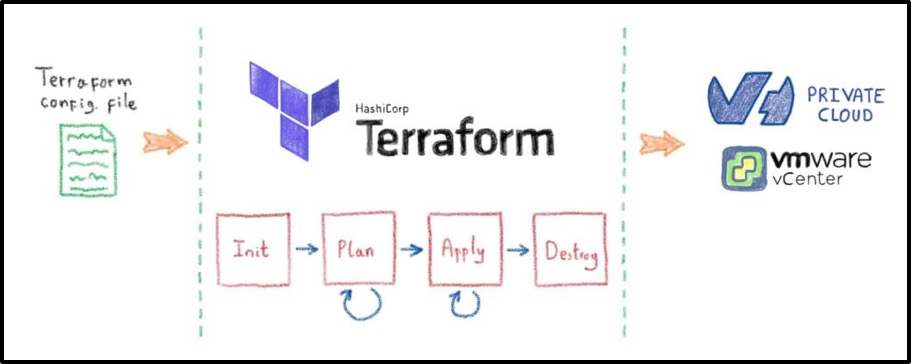
Terraform
Terraform is a multi-cloud (IaC) Infrastructure as Code software by HashiCorp written in Go Language using (HCL) HashiCorp Config Language. An open-source command line tool can be used to provide an infrastructure on many different platforms and services such as IBM, AWS, GCP, Azure, OpenStack, VMware, and more.
Using a plugin-based model to support providers and provisioners, gives the ability to support almost any service that exposes APIs. It is a cloud-agnostic tool that elegantly defines your IaC, simple and yet powerful; Terraform allows you to build complex, version-controlled, collaborative, heterogeneous, and disposable systems with very high productivity.
It provides built-in dependencies between each tier that handle the automatic provisioning of infrastructure, both in the public and private cloud. Whereas configuration management and server templating tools define the code that runs on each server, server provisioning tools such as Terraform, CloudFormation, and OpenStack Heat are responsible for creating the servers themselves.
In fact, you can use provisioning tools to not only create servers, but also databases, caches, load balancers, queues, monitoring, subnet configurations, firewall settings, routing rules, SSL certificates, and almost every other aspect of your infrastructure.
For example, the following code deploys a web server using Terraform:
resource "aws_instance" "app" {
instance_type = "t2.micro"
availability_zone = "us-east-1a"
ami = "ami-40d28157"
user_data = <<-EOF
#!/bin/bash
sudo service apache2 start
EOF
}
AWS CloudFormation
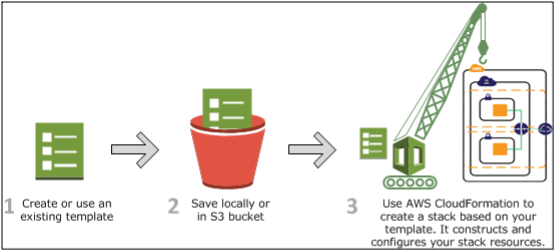
AWS CloudFormation is a service that helps you model and set up your Amazon Web Services resources. This is so you can spend less time managing those resources and more time focusing on your applications that run in AWS.
You create a template that describes all the AWS resources that you want (like Amazon EC2 instances, or Amazon RDS DB instances), and AWS CloudFormation takes care of provisioning and configuring those resources for you. You don't need to individually create and configure AWS resources and figure out what's dependent on what; AWS CloudFormation handles all of that.
Key Features:
- Improved automation: The simplicity of the template allows you to declare what you want your resources to look like. This eliminates the need to rely on other scripting tools to create the resources.
- Quick infrastructure replication: You can quickly replicate your infrastructure without affecting other resources that your template previously created. The template can be used to create as many stacks as needed.
- Infrastructure consistency: The declarative way of defining templates allows for consistency—you can be assured that stacks created with the template will be identical.
- Easy-to-read template: If you are in the web application or micro-service space, you have used yaml or JSON at some point. They are both widely used, therefore making it easy to understand or find resources on it.
There are three concepts you need to be aware of when using CloudFormation, and these concepts are fundamental to how it works:
- Template
- Stack
- Change Set
Template
A template is a declarative way of defining your resources as a yaml or json file. This template can then be used to deploy the resources either using the console or CLI. This demo.yaml template shows an example of a yaml template file that creates an EC2 instance and Elastic IP and attaches the IP to the instance.
AWSTemplateFormatVersion: "2010-09-09"
Description: A demo template
Resources:
MyEC2Instance:
Type: "AWS::EC2::Instance"
Properties:
ImageId: "ami-0f7919c33c90f5b58"
InstanceType: t2.nano
KeyName: testkey
MyEIP:
Type: AWS::EC2::EIP
Properties:
InstanceId: !Ref MyEC2Instance
Stack
When you deploy a template like the example we had above, it creates both resources (EIP and EC2) as a stack. These resources are created as a unit; therefore, any update or deletion of resources will be applied to the stack. You can use a single template to create multiple stacks as long as there are no naming conflicts.
Change Set
When a stack needs to be updated, you can simply run an update on the stack and let AWS take care of replacing the necessary resources. Change Set takes that further and gives you the ability to see the impact of the changes you are applying before they are actually applied. In the terraform world this would be equivalent to terraform plan.
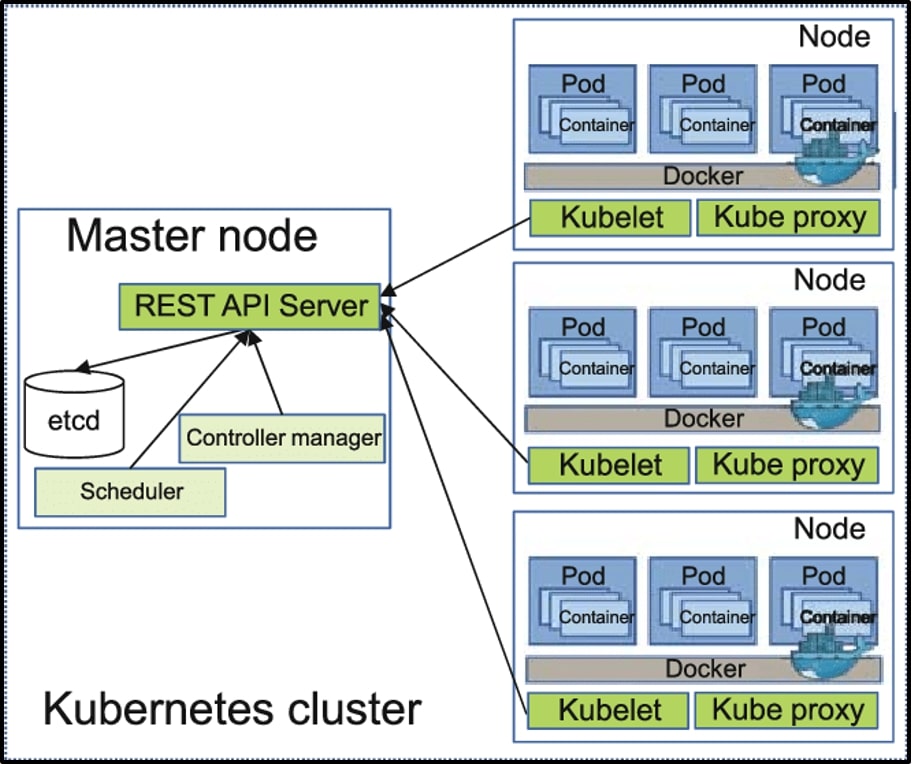
Kubernetes
With the widespread adoption of containers among organizations, Kubernetes, the container-centric management software, has become the de facto standard to deploy and operate containerized applications. Google Cloud is the birthplace of Kubernetes—originally developed at Google and released as open-source in 2014.
Kubernetes builds on 15 years of running Google's containerized workloads and the valuable contributions from the open-source community. Inspired by Google’s internal cluster management system, Borg, Kubernetes makes everything associated with deploying and managing your application easier.
Providing automated container orchestration, Kubernetes improves your reliability and reduces the time and resources attributed to daily operations. Kubernetes (sometimes shortened to K8s with the 8 standing for the number of letters between the “K” and the “s”) is an open-source system to deploy, scale, and manage containerized applications anywhere.
To learn more about Kubernetes, you can also check out our MetricFire article which explains Kubernetes in great detail.
Key Features:
- Automated operations: Kubernetes has built-in commands to handle a lot of the heavy lifting that goes into application management, allowing you to automate day-to-day operations. You can make sure applications are always running the way you intended them to run.
- Infrastructure Abstraction: When you install Kubernetes, it handles the computing, networking, and storage on behalf of your workloads. This allows developers to focus on applications and not worry about the underlying environment.
- Service Health Monitoring: Kubernetes continuously runs health checks against your services, restarting containers that fail, or have stalled, and only making available services to users when it has confirmed they are running.
Conclusion
I hope by now you have enough information about various cloud automation tools and are able to make the right choice for your organization. Once you decide on these models we highly recommend collecting a rich set of metrics to monitor your infrastructure. If you need help setting up, feel free to reach out to me through LinkedIn.
Additionally, MetricFire can help you monitor your applications across various cloud models. Robust monitoring will not only help you meet SLAs for your application but also ensure a sound sleep for the operations and development teams.
Monitoring is extremely essential for any application stack, and you can get started with your monitoring using MetricFire’s free trial. If you would like to learn more about it and talk to our experts, please book a demo with us.